Unbreakable Like Diamond | What Is AES-256 Encryption?
When something is valuable, we either hide it somewhere or lock it up real good. In the digital world, we can easily do both effortlessly….

Table of Contents
Protect your online privacy and security
Fast, private, and easy to use, get Hidzo on your device and browse freely with one tap.
Get HidzoVPN
When something is valuable, we either hide it somewhere or lock it up real good. In the digital world, we can easily do both effortlessly. AES-256 is a code word for “don’t worry, a nuclear bomb might destroy your files, but it can’t decrypt them.” We’re talking about a security algorithm that all resources on planet earth combined can’t breach; we’re talking about a mathematical masterpiece that secures your:
- file sharing and storage, online and offline.
- online transactions and finances.
- whole online social life.
- wireless router.
A Plain-English Explanation of AES-256
Let’s paint a picture; your file is a piece of jewelry in a vault. Here, the vault is an Advanced Encryption Standard or AES, and the 256 is the combination to your safe. However, a standard vault doesn’t compare to AES-256 in a million years, literally!
When a file or a message is encrypted via AES-256, anyone who doesn’t have the key has to try different keys (=brute-force attack) to open, or more exactly, decrypt the message.
Let’s get back to our analogy to help you understand the magnitude of the strength of AES-256. Our metaphorical vault will have to have as many combinations as the number of stars in the observable universe. The number of stars in each galaxy is roughly 10^11, and there are approximately 2 trillion galaxies in the world. You do the math if you’re an alien. Simply put, AES-256 is not breakable in the foreseeable future.
There are two other variants of AES with different key lengths, namely AES-128 and AES-192. These are also very strong, but the longer the key, the stronger the encryption.
| Encryption | Possible Keys | Possible keys in natural numbers |
|---|---|---|
| AES-128 | 2^128 | 340282366920938463463374607431768211456 |
| AES-192 | 2^192 | 6277101735386680763835789423207666416102355444464034512896 |
| AES-256 | 2^256 | 115792089237316195423570985008687907853269984665640564039457584007913129639936 |
6 Critical Places AES-256 Secures Your Life
You might think AES-256 is good for government secrets, like the whereabouts of that nuclear submarine in the Pacific Ocean. Well, yes, but your secrets are just as important. In fact, you’re using AES-256 on a daily basis without knowing it.
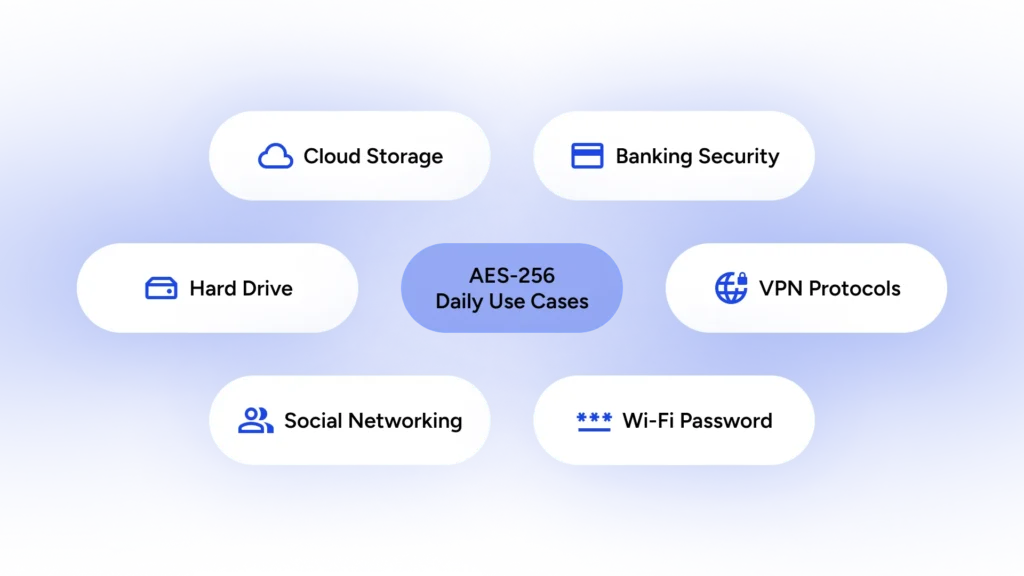
1. HTTPS Websites and Banking Transactions
Have you noticed the Lock icon next to the address bar in your browser? That means what is being transferred from your browser to the website and vice versa is encrypted using AES-256 encryption. This encryption is on for all HTTPS websites, whether it’s Amazon, Gmail, your bank’s website, or any other website secured with HTTPS.
2. Secure Messaging
This is where AES-256 secures a path between you and your contact in a process called End-to-End Encryption. Let’s take Telegram, for instance. When you start a chat with someone, all your messages are encrypted with a key that only you and the recipient have.
3. Disk Encryption
The hard drives on your PC, laptop, MacBook, etc., are encrypted via AES-256. The encryption is on by default on all up-to-date Mac devices and Windows devices with a legal license.
However, you might want to use third-party encryption apps like WinRAR to add another layer of god-knows-how-strong security to your file. Just a warning, if you used WinRAR to secure a file, and you forgot the password, there’s no way in the world to recover it; it’s like a Bitcoin sent to an invalid address.
4. Cloud Storage
Cloud storage is mainly used for backup and seamless file sharing between devices. When you upload a file to cloud storage, they put the data at rest. Cloud service providers use AES-256 to secure your files. Therefore, even if their database is breached, no one can decrypt your files.
5. Wi-Fi Password
One of the several encryption methods available on wireless routers is AES, which makes the data indecipherable for unauthorized parties, that is, anyone who doesn’t have the key.
When you set the authentication type to WPA2, the data that is transferred between your device (e.g., cell phone, smart TV, etc.) and the router is encrypted with AES-128. On newer routers, WAP3 is also available, which gives you the option to use AES-256.
6. VPN Security Benefits
A VPN is an indispensable privacy protection tool. Going online without a VPN is like going out in the real world wearing see-through clothes. VPNs use several protocols to make a virtual tunnel in your internet connection. On one end of this tunnel is your phone, and on the other is the VPN server.
Among the several features of using a VPN is the encryption of your data. VPN protocols, such as OpenVPN, use AES-256 for VPN encryption of the data that travels between your device and the VPN server. Therefore, even if the data packets are intercepted along the way, they are utterly indecipherable.
Looking for a VPN?
HidzoVPN is a secure and fast VPN that uses a smart protocol called Vless XTLS TCP, which adapts to your internet connection to maximize stability. HidzoVPN has implemented the Kill Switch feature to ensure nothing gets leaked if your connection is lost for any reason. Yet, the best thing about HidzoVPN is its affordable price. You can purchase HidzoVPN Premium for just $2.99/mo.
How AES-256 Protects Your Data Like a Fortress
AES-256 breaks your data into 128-bit (16-byte) data blocks and encrypts each block separately in 14 rounds. Each round consists of 4 stages:
- SubBytes: Swaps bytes using a lookup table.
- ShiftRows: Shifts rows in the block like a Rubik’s Cube.
- MixColumns: Mixes columns mathematically.
- AddRoundKey: XORs with a part of the key.
What happens in these four stages is basically the scrambling of the data blocks to make them look entirely random and unrelated.
If you’re still in the dark about how AES-256 works, it’s because it’s too complicated, and we have the above numbers and figures to vouch for this. But, if you’re a visual learner AES Explained can make things clearer.
The Achilles’ Heel of AES-256
AES-256 is utterly robust and solid in itself, no doubt about it. However, the way it’s implemented, that is, the coding, and human error can jeopardize data security. The Achilles’ Heel of AES-256 is side-channel attacks and key management.
Of course, these threats do not inherently undermine the mathematical foundations of the encryption algorithm itself, but can compromise the security of the encrypted data by enabling unauthorized access or decryption.
FAQs
It refers to the Advanced Encryption Standard with a 25-bit key length. The term military-grade encryption is used to denote government-approved cryptographic methods to encrypt National-Security-Level secrets.
Mathematically speaking, yes. AES-256 is utterly unbreakable with current technology.
Even with millions of supercomputers, it would take millions of years to decrypt AES-256.




